BGP Blackholing
This is a method of initiating blackholing in the event of a DDoS attack using an upstream service.
This works in the following stages:
- Announcement: The victim AS under attack announces the targeted destination IP or prefix to its upstream provider or Internet Exchange Point (IXP).
- Propagation: The upstream provider or IXP then advertises a more specific prefix and modifies the next-hop address to divert the traffic to a null interface.
- Blackhole Community: The blackholing message is tagged with a specific BGP Communities attribute to differentiate it from regular routing updates. This is normally the community 666.
There are two main ways this is implement.
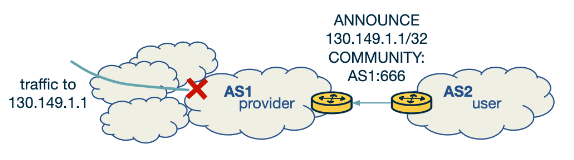
- Using an Upstream Provider:
- The victim network announces a blackholing message to its upstream provider, specifying the attacked IP and the blackholing community.
- The provider then recognises this message and sets the next-hop field to a blackholing IP, effectively discarding all traffic to the attacked IP.
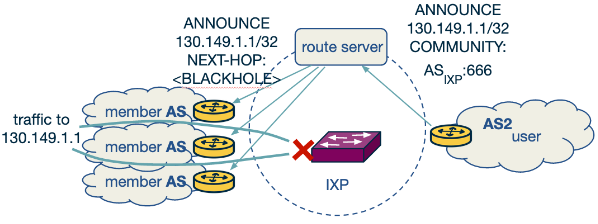
- Using an Internet Exchange Point (IXP):
- If the victim network is part of an IXP, it sends a blackholing message to the IXP route server.
- The route server then propagates this message to all connected IXP member networks, which drop the traffic to the blackholed IP.
Key Benefits of BGP Blackholing:
- Effective Mitigation: Stops high-volume attacks close to their source, preventing them from reaching and overwhelming the target.
- Scalability: Can be implemented quickly by upstream providers or IXPs to protect multiple networks.
- Cost-Efficiency: Reduces the need for expensive DDoS mitigation services by leveraging existing BGP infrastructure.
Challenges and Considerations:
- Collateral Damage: Legitimate traffic to the blackholed IP is also dropped, which can disrupt normal operations.
- Coordination: Effective implementation requires coordination and trust between the victim network and its upstream providers or IXPs.
- Community Attributes: The blackhole community attributes must be publicly available and correctly implemented to ensure proper functioning.